Context:
Recently, the Standing Committee on Finance submitted its report on ‘Cyber Security and Rising Incidence of Cyber/White Collar Crimes’.
Key Observation and Recommendation of the Standing Committee on Finance:
About Cyber Security:
| Concern | Recommendation | |
| Regulation of Service Providers | Challenges in control over third-party service providers on cyber security matters, especially with big tech and telecom companies. | Enhance regulatory powers to oversee and control service providers, including big tech and telecom companies. Ensure their compliance with security standards and collaboration with regulatory bodies like the Reserve Bank of India (RBI). |
| Critical Payment Systems | Critical payment systems, essential for customer services, are not currently regulated, leading to disruptions and downtime. | Encourage closer collaboration between critical payment systems and financial institutions. Invest in infrastructure, conduct regular security assessments, and establish incident response mechanisms to ensure improved uptime and stability. |
| Complex Regulatory Landscape | Multiple agencies and bodies in the regulatory landscape result in challenges of coordination and efficient response to cyber threats. | Establish a centralized Cyber Protection Authority (CPA) to streamline regulatory efforts and coordination. This central authority can develop and implement unified cyber security policies, guidelines, and best practices. |
| Challenges faced by smaller financial institutions | Smaller financial institutions, like cooperative banks and NBFCs, face more cyber security incidents due to limited resources and technological capabilities. | Prioritize investments in cyber security infrastructure, advanced threat detection systems, and secure data storage practices. Conduct regular audits and assessments to identify vulnerabilities and bridge the gap in cyber security measures. |
| Inadequate Cyber Security Audits | Significant disparity in conducting cyber security audits, with only 11% of cooperative banks having undertaken such audits. | Ensure that all financial institutions, irrespective of size, conduct regular cyber security audits. Promote the adoption of best practices and encourage smaller entities to invest in cyber security measures. |
| Digital Landscape Vulnerability | The expansion of digital landscapes and the presence of search engines and tech companies increase vulnerability to cybercrime, including data breaches and fraudulent activities | Mandate application stores to share comprehensive metadata and information about hosted applications. Tech companies should maintain updated systems, patch vulnerabilities, and enforce stringent vetting processes for app approvals. |
| Compensation for Frauds | The existing compensation mechanism for cybercrime victims in the financial sector has limited scope, complex processes, and places the burden of proof on victims. | Shift the responsibility of compensating customers in cases of fraud from victims to financial institutions. This would provide more support to victims and encourage institutions to take preventive measures against cybercrime. |
| Inadequate Enforcement | The Information Technology Act, 2000, faces challenges of inadequate enforcement and the bailable nature of most offenses, allowing fraudulent activities to persist. | Strengthen the Information Technology Act by implementing stricter penal provisions, imposing stricter bail conditions, and considering provisions for local surety. |
| Central Negative Registry | The Committee recommended the creation of a Central Negative Registry which would be maintained by the CPA. The registry should consolidate information on fraudsters’ accounts. The registry should be made available to banks and NBFCs which would proactively deter and prevent the opening of accounts associated with fraudulent activities. | |
- Cybersecurity refers to the practice of protecting computer systems, networks, devices, and digital information from unauthorized access, data breaches, cyber-attacks, and other forms of unauthorized exploitation.
- It encompasses a range of strategies, technologies, and practices designed to ensure the confidentiality, integrity, and availability of digital assets.
- Network Security: Ensuring the security of networks by implementing firewalls, intrusion detection systems, intrusion prevention systems, and virtual private networks (VPNs) to prevent unauthorized access and attacks.
- Endpoint Security: Protecting individual devices, such as computers, smartphones, and tablets, by using antivirus software, anti-malware programs, and encryption to secure data and prevent infections.
- Application Security: Securing software applications by identifying and patching vulnerabilities, conducting code reviews, and implementing secure development practices to prevent exploitation and unauthorized access.
- Cloud Security: Protecting data and applications stored in cloud environments by using encryption, access controls, and multi-factor authentication to ensure data privacy and prevent data breaches.
- Data Security: Implementing measures such as encryption, access controls, and data loss prevention (DLP) tools to safeguard sensitive data from unauthorized access, theft, or leaks.
- Increasing Cybercrimes:
- According to the NCRB’s “Crime in India, 2020” report, cybercrimes have increased by 306 percent in the past four years.
- Ransomware Incidents: The “India Ransomware Report 2022” published by CERT-In highlights a 53 percent increase in ransomware incidents in 2022 compared to the previous year.
- Financial Crime Volume: In the financial year 2020-21, there were 2.62 lakh reported financial crimes. This number increased significantly to 6.94 lakhs in the year 2022.
- Domestic Payments Fraud: In FY 2021, regulated entities in India reported domestic payments fraud amounting to Rs 542.7 crore. This figure escalated to Rs 2537.35 crore in FY 2023.
- Digital Loan Apps Frauds: In the year 2022, there were 26,844 fraud cases related to digital loan apps. This number decreased to 9,926 in the year 2023.
- Digital Transformation (Digital India): A report projects that the value of digital payments in India is expected to grow from 300 billion dollars in FY21 to close to 1 trillion dollars in FY26.
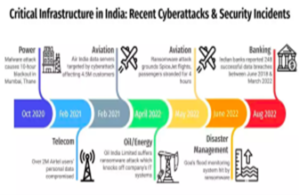
- Critical Infrastructure Protection: India’s critical infrastructure, including power plants, healthcare facilities, railways, and banking systems, has been under increasing cyber threats.
- Terrorism and Hacktivism: The International Institute for Counter Terrorism’s report highlights the rise in hacktivism activities in Southeast Asia, including distributed denial-of-service (DDoS) attacks and information leaks.
- Hacktivism is the act of hacking, or breaking into a computer system.
- Global Initiatives:
- Budapest Convention on Cybercrime (2001): An international treaty that harmonizes national laws, improves investigative techniques, and enhances cooperation among nations to address cybercrime.
- It deals with issues such as infringements of copyright, computer-related fraud, child pornography and violations of network security.
- India is not a signatory to this convention, it has relevance on the global stage.
- Global Centre for Cyber Security: It is an initiative of the World Economic Forum with its headquarters in Geneva.
- Aims: To establish the first global platform for governments, businesses, experts and law enforcement agencies to collaborate on cyber security challenges.
- Paris call: At the UNESCO Internet Governance Forum (IGF) meeting convened in Paris, “The Paris Call for Trust and Security in Cyberspace” was commenced, aimed at developing common principles for securing cyberspace.
- Budapest Convention on Cybercrime (2001): An international treaty that harmonizes national laws, improves investigative techniques, and enhances cooperation among nations to address cybercrime.
- India’s Initiatives:
- Institutional Measures:
- National Critical Information Infrastructure Protection Centre (NCIIPC): Operates as the nodal agency for protecting and ensuring the resilience of critical information infrastructure.
- Indian Cyber Crime Coordination Centre (I4C): Established in 2020 to handle various types of cybercrimes in a comprehensive and coordinated manner.
- Cyber Surakshit Bharat Initiative: Launched in 2018 to spread awareness about cybercrime and enhance capacity-building for Chief Information Security Officers (CISOs) and IT staff in government departments.
- Cyber Swachhta Kendra: Introduced in 2017, this platform helps users clean their devices by removing viruses and malware.
- National Cyber Crime Reporting Portal: A citizen-centric platform enabling online reporting of cybercrimes, with complaints accessed by relevant law enforcement agencies.
- National Cyber Security Policy 2013: The government released the National Cyber Security Policy 2013 to safeguard both physical and business assets of the country.
- National Cyber Security Strategy 2020: It was formulated by the Office of National Cyber Security Coordinator at the National Security Council Secretariat. It aims to improve cyber awareness and cybersecurity through more stringent audits.
- Computer Emergency Response Team – India (CERT-In): Under the Ministry of Electronics and Information Technology, CERT-In collects, analyzes, and disseminates information on cyber incidents and issues cybersecurity alerts.
- Legislative Measures:
- Information Technology Act, 2000: Regulates the use of computers, computer systems, networks, data, and information in electronic format.
- India’s draft Digital Personal Data Protection Bill 2023: The Union Cabinet cleared the Digital Personal Data Protection (DPDP).
- No procedural code: There is no separate procedural code for the investigation of cyber or computer-related offences.
- Admissibility of Electronic Evidence: The complexities around the admissibility of electronic evidence have created uncertainty in legal proceedings, requiring clear guidelines for the admissibility of electronic records.
- Jurisdiction and Enforcement: Most cybercrimes have a trans-national nature, leading to challenges in collecting evidence from foreign territories and dealing with cross-border legal complexities.
- Technical Staff Shortage: There’s a shortage of technically qualified staff within law enforcement agencies to effectively investigate cybercrimes, as electronic evidence requires specialized knowledge.
- Ex., In the Aarushi murder case of Noida, reported as Dr. (Smt.) Nupur Talwar vs State of U.P. and Anr., the Allahabad High Court observed that the Indian Computer Emergency Response Team (CERT-IN) expert was not provided with the details of the Internet logs, router logs and laptop logs to prove whether the Internet was physically operated on the fateful night.
- Capacity Building: Invest in training and recruiting technically qualified personnel within law enforcement agencies to handle cybercrimes effectively.
- Clear Admissibility Rules: Develop and implement clear guidelines for the admissibility of electronic evidence in court, based on recent legal judgments and international standards.
- Inadequate Cyber Infrastructure: The need for upgraded and modernized cyber forensic laboratories, equipped to handle emerging technologies and digital evidence, is essential but currently inadequate.
- Enhanced Collaboration: Promote collaboration between the central and state governments to create uniform statutory procedures for enforcement agencies and provide sufficient funds for developing cyber infrastructure.
- Data Localisation: Enact legislation that includes ‘data localization’ provisions to enable enforcement agencies to access the data of suspected Indian citizens promptly.
Post Views: 189
